Automated Deployment of Application Observability Platform
Introducing the Service Foundry Suite for Observability
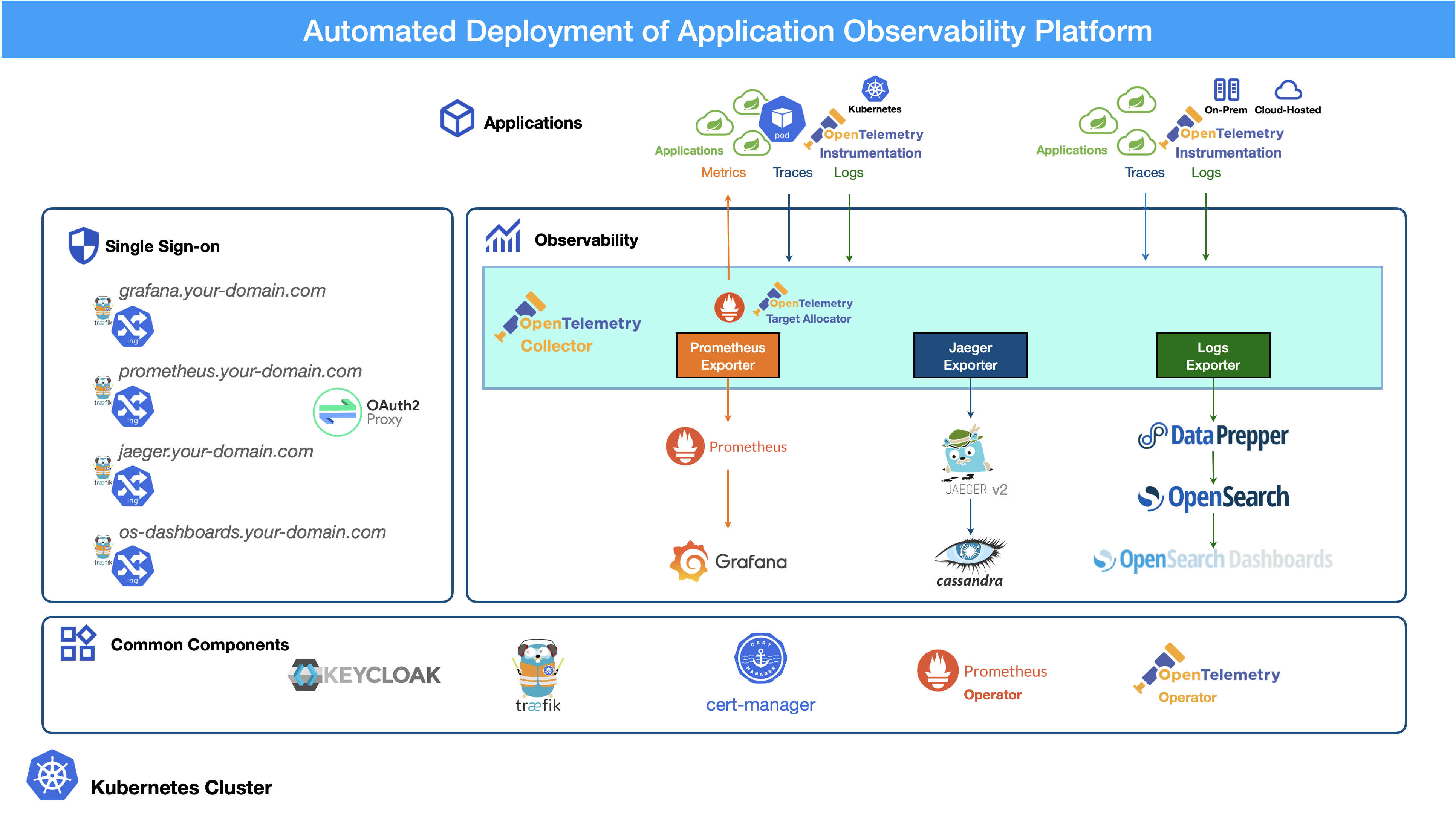
We’re excited to announce the official release of the Service Foundry Suite—a fully automated, Kubernetes-native solution for deploying and managing modern observability stacks.
This suite streamlines the deployment of observability components using Helm charts, Kubernetes Jobs, and best practices for DevOps integration.
Suite Components Overview
infra-foundry
Deploys foundational infrastructure for observability:
-
Keycloak – Identity and access management
-
Traefik – Ingress controller with SSO middleware support
-
cert-manager – Manages TLS certificates automatically
-
Prometheus Operator – Simplifies Prometheus setup and operations
-
OpenTelemetry Operator – Manages OpenTelemetry Collectors
o11y-foundry
Builds the telemetry pipeline and visualization layers:
-
OpenTelemetry Collector & Target Allocator – Collects logs, traces and metrics
-
Jaeger + Cassandra – Distributed tracing with persistent storage
-
Data Prepper – Parses and routes log data
-
OpenSearch & OpenSearch Dashboards – Log aggregation and visualization
-
Prometheus & Grafana – Metrics collection and dashboards
sso-foundry
Enables SSO across observability tools:
-
OAuth2 Proxy – Provides authentication
-
Traefik Ingress Controllers – Routes secure access to:
-
jaeger.yourdomain.com
-
os-dashboards.yourdomain.com
-
prometheus.yourdomain.com
-
grafana.yourdomain.com
-
What is Service Foundry
Service Foundry is a Kubernetes-native platform for deploying turnkey applications. It simplifies cloud-native development by providing reusable deployment patterns and modular Helm charts tailored for enterprise-scale observability and infrastructure management.
What is Observability
Observability is the ability to understand the internal state of a system using telemetry data: logs, metrics, and traces. It enables real-time monitoring, performance analysis, and debugging in distributed applications.
OpenTelemetry Overview
OpenTelemetry is a vendor-neutral, open-source observability framework offering APIs and agents to collect logs, metrics, and traces from cloud-native applications.
Key capabilities:
-
Centralized logging: Logs collected by OpenTelemetry → processed by Data Prepper → stored in OpenSearch
-
Distributed tracing: Traces collected and visualized via Jaeger, stored in Cassandra
-
Metrics Collection: Metrics collected by OpenTelemetry → stored in Prometheus → visualized with Grafana
Zero-Code Instrumentation
Zero code instrumentation is a key feature of OpenTelemetry that allows developers to collect telemetry data from their applications without modifying the application code. This is achieved through the use of OpenTelemetry auto-instrumentation libraries, which automatically instrument the application and collect telemetry data at runtime. This makes it easy to add observability to existing applications without requiring any code changes or manual instrumentation.
Metrics collected by OpenTelemetry → stored in Prometheus → visualized with Grafana
Download the agent:
Example usage:
$ java -javaagent:opentelemetry-javaagent.jar -jar otel-spring-example.jarKey environment variables:
-
OTEL_EXPORTER_OTLP_ENDPOINT - the endpoint of the OpenTelemetry Collector
-
OTEL_LOGS_EXPORTER - the exporter to use for logs (e.g., otlp, jaeger, zipkin)
-
OTEL_TRACES_EXPORTER - the exporter to use for traces (e.g., otlp, jaeger, zipkin)
-
OTEL_METRICS_EXPORTER - the exporter to use for metrics (e.g., otlp, prometheus)
OpenTelemetry Collector & Target Allocator
-
Collector - Receives, processes, and exports telemetry data
-
Target Allocator - Dynamically assigns scrape targets for metrics collection
Service Foundry uses this to automate metrics collection from OpenTelemetry-instrumented apps.
Enabling SSO for Open Source Tools
Many observability tools (Jaeger, Grafana, Prometheus, OpenSearch Dashboards) lack built-in SSO. sso-foundry addresses this gap by:
-
Deploying OAuth2 Proxy for SSO authentication
-
Using Traefik to manage routing based on domain
-
Delegating user authentication and access control to Keycloak
Get Started with Service Foundry
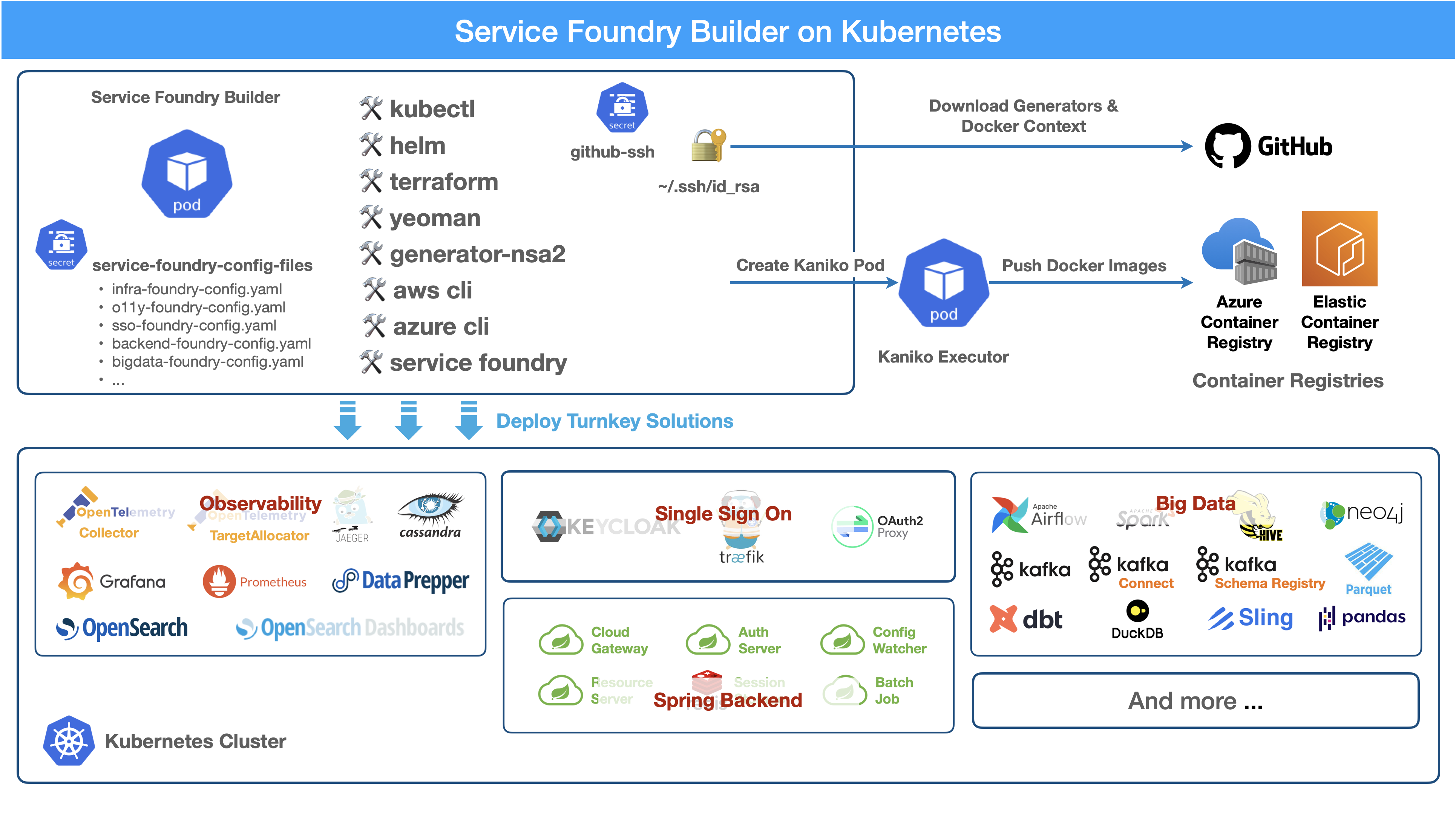
Service Foundry Builder
Service Foundry Builder is a tool for building and deploying applications in a Kubernetes environment. It provides a set of tools and best practices for building, deploying, and scaling applications in a cloud-native way.
GitHub SSH key is required to run Service Foundry Builder. Contact the Service Foundry team to get the SSH key.
1. Add the Helm Repository
$ helm repo add service-foundry https://nsalexamy.github.io/helm-charts2. Create a Namespace
$ kubectl create namespace service-foundry3. Create AWS Secret
$ kubectl -n service-foundry create secret generic aws-secret \
--from-literal=AWS_ACCESS_KEY_ID=$AWS_ACCESS_KEY_ID \
--from-literal=AWS_ACCOUNT_ID=$AWS_ACCOUNT_ID \
--from-literal=AWS_SECRET_ACCESS_KEY=$AWS_SECRET_ACCESS_KEY \
--from-literal=AWS_REGION=$AWS_REGION4. Create GitHub SSH Secret
$ kubectl -n service-foundry create secret generic service-foundry-github-ssh \
--from-file=./id_rsa --from-file=./id_rsa.pub5. sAdd Configuration Files
$ kubectl create secret generic service-foundry-config-files \
--from-file=infra-foundry-config.yaml \
--from-file=o11y-foundry-config.yaml \
--from-file=sso-foundry-config.yaml \
-n service-foundry6. Install the Builder Helm Chart
$ helm install service-foundry-builder service-foundry/service-foundry-builder \
-n service-foundry --create-namespace7. Monitor Resource Creation
You can monitor created resources via the AWS Console:
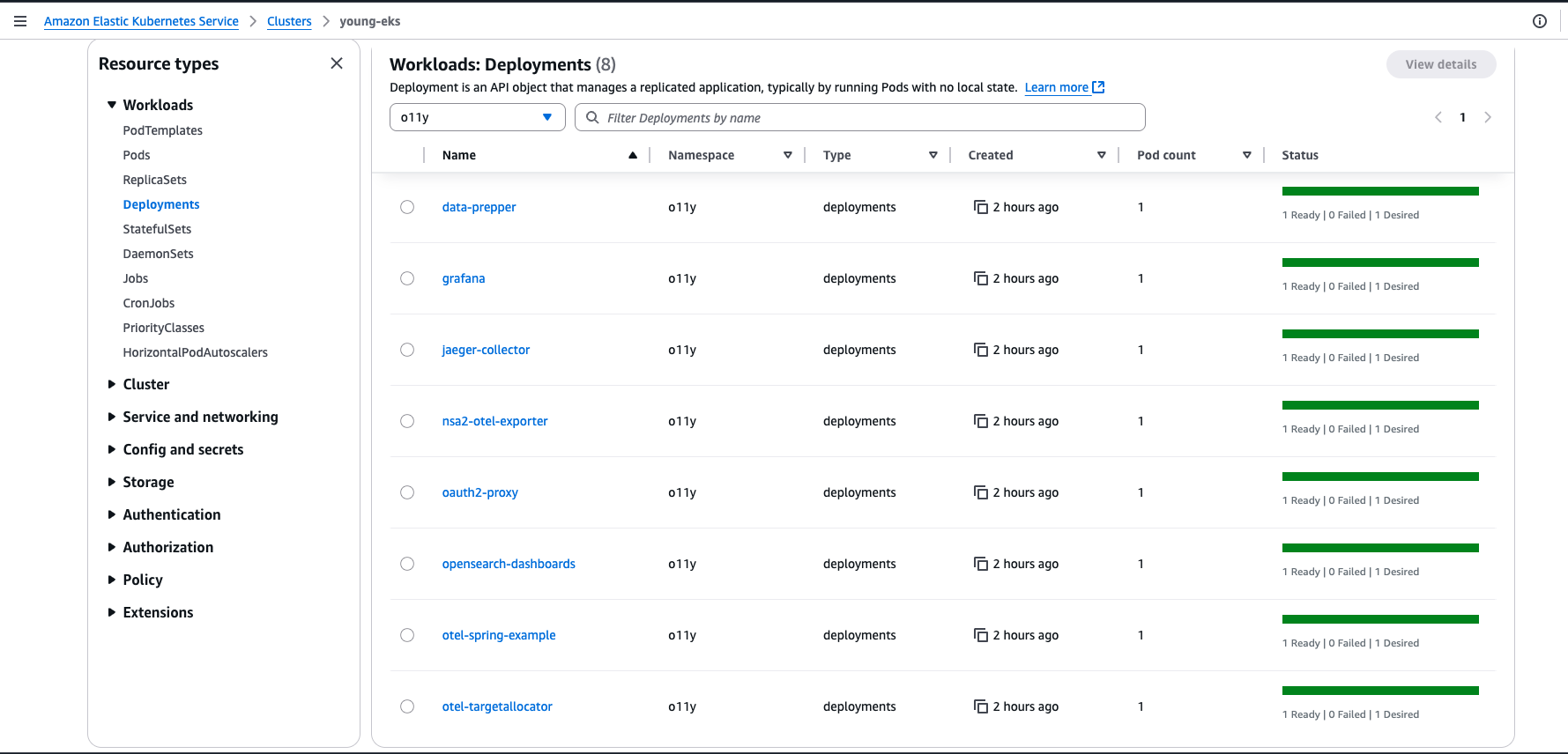
8. Clean Up Resources
To clean up the resources created by Service Foundry Builder, you can use the following command:
$ kubectl create secret generic service-foundry-config-files \
--from-file=infra-foundry-config.yaml \
--from-file=o11y-foundry-config.yaml \
--from-file=sso-foundry-config.yaml \
-n service-foundry --set command=cleanUse the --set command=clean flag to safely tear down the environment.
🎥 Request a Live Demo
Want to see it in action?
-
📨 Email: credemol@gmail.com
-
💬 LinkedIn DM: https://www.linkedin.com/in/credemol/
🌐 What the Demo Covers
-
✅ Full deployment using Amazon EKS and ECR
-
✅ Requires AWS credentials (AWS_ACCESS_KEY_ID, AWS_ACCOUNT_ID, etc.)
-
✅ Automated Helm-based deployment via Service Foundry Builder
-
✅ Deploys infra-foundry, o11y-foundry, and sso-foundry
-
✅ Keycloak initialized via Terraform
-
✅ Traefik and OAuth2 Proxy for secure SSO
-
✅ TLS certificates managed by cert-manager
-
✅ OpenTelemetry forms the observability backbone
-
✅ Metrics, traces, and logs visualized via Grafana, Jaeger, OpenSearch Dashboards
-
✅ Sample Spring Boot app auto-instrumented with OpenTelemetry Java agent